Log Management & SIEM
ProLog - Your powerful tool for
IT security
IT security made in Germany.
ProLog combines log management & SIEM: for maximum data, IT and audit security in your company.
ProLog is the powerful IT security solution from Germany that combines professional log management with SIEM. It was specially developed for critical infrastructures and therefore offers you the highest security standard.
With ProLog, you implement indispensable basics that your company needs for fundamentally secure IT - consisting of technical and organizational measures. At the same time, you meet important requirements that an auditor places on your IT security - for example in the context of IT-SiG 2.0, DGSVO or ISO27001.

Log management explained in 90 seconds
Your advantages with ProLog
Store, manage and analyze log data in a tamper-proof manner
Detect threats & anomalies at an early stage
Immediate alerting of critical conditions in IT systems
Increase IT security
Meet legal requirements for IT security
Optimally complement existing systems
Security for the next IT audit
Data forensics and case analysis
How can you use ProLog in your company?
We would be happy to advise you personally on this.
All in one package!
With ProLog you get a comprehensive concept
Detailed documentation
ProLog Software
Ready-made reporting and alerting packages
Regular maintenance & updates
Predictable costs thanks to user-based licensing model
In contrast to most comparable solutions on the market, ProLog is licensed on the basis of Active Directory (AD) users as a purchase or rental price model.
Your advantage: You do not have to worry about cost explosions due to increasing data volumes.
The cost calculation of SIEM solutions is based either on the number of AD users, the number of log sources or the log volume (number of logs and data size). Depending on the calculation basis, there are different advantages and disadvantages. The graphic gives you a brief overview. We would also be happy to advise you personally.
Sample calculation: Cost comparison over 5 years

Comparable
SIEM solutions
60.000 €
Calculation basis: 50 log sources Annual rental costs: € 12,000

ProLog
11.250 €
Calculation basis: 50 AD users One-off purchase costs: € 6,250
Annual maintenance: € 1,250
ProLog is the optimal solution for your company if
-
You want to protect your IT systems from cyber attacks.
-
you have to meet legal requirements (CRITIS).
-
you want to protect your company from the severe consequences of cyberattacks.
-
have no or too little own capacities for your log management.
-
They lack the know-how with regard to comprehensive IT security.
-
you are looking for a simple solution for the complex requirements of secure IT.
Let's work together to improve your IT security and minimize your concerns
about data protection and cyber attacks.
Fast commissioning within a few weeks
FAQ
With Log Management, all of your company's log data is collected in a central location, normalised and stored in a tamper-proof manner. Numerous regulatory requirements mandate the design and implementation of a log management solution. Learn more.
The Security Information and Event Management (SIEM) analyses and correlates this log data in real time. This allows complex events to be recognised in time, responsible persons to be informed by means of an alarm and countermeasures to be initiated.
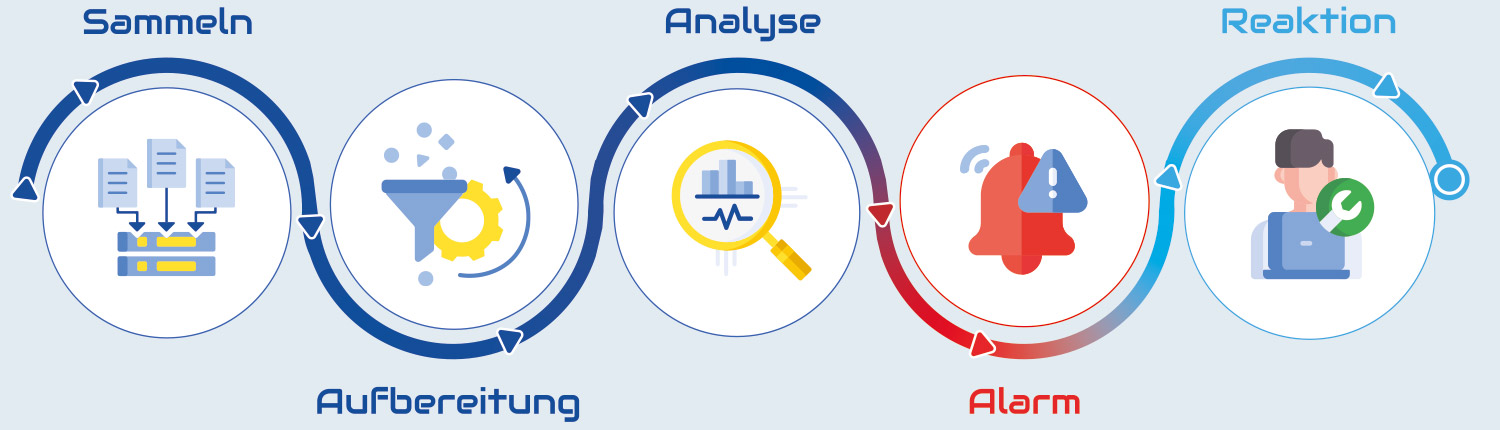
Log data, also known as log files, log files or logs, are files in which computer processes log a wide variety of events. Logs are automatically generated by software, operating systems, network devices, and other IT components. They capture various types of information, such as user activity, login attempts, network connections, system events, error messages, security alerts, data accesses, and transactions.
Log Management enables the central collection, storage, monitoring and analysis of log data. This results in three important features that make Log Management important for your IT security:
- Detect threats early: By integrating log management solutions with SIEM systems, logs can be monitored in real time, analyzed, and matched against predefined rules or behavior patterns to identify potential threats.
- initiate countermeasures: In addition, vulnerabilities in IT systems can be identified and appropriate countermeasures can be taken.
- Forensic Analysis: Log management plays a critical role in forensic analysis of security incidents. By recording events in detail, logs enable the reconstruction of attacks, identification of entry points, and investigation of impact.
Every single company is exposed to the risks of a cybersecurity incident - regardless of the industry and the size of the company. That's why it basically makes sense for every company to ensure secure IT and implement a central log management system like ProLog.
However, "only" operators of critical infrastructures are currently legally obligated to do so.
According to Section 2(10) of the BSIG, this includes facilities, installations or parts thereof belonging to the following sectors:
- Energy
- Information technology and telecommunications
- Transportation and traffic
- Health
- Media and culture
- Water
- Nutrition
- Finance and insurance
- Municipal waste management
- State and administration
If your company does not fall under the BSI Criticality Ordinance, we still recommend that you set up your IT infrastructure securely and reliably. We will be happy to advise you on this.
In Germany, various legal requirements apply with regard to log management. These include, among others:
- General Data Protection Regulation (DSGVO): According to the DSGVO, personal data must be treated securely and confidentially. Log data that contains personal information is subject to the provisions of the DSGVO.
- Federal Data Protection Act (BDSG): The BDSG regulates the protection of personal data in Germany. It contains specific regulations on data security and the handling of log data.
- IT Security Act (IT-SiG): The IT-SiG obliges operators of critical infrastructures (KRITIS) to take appropriate organizational and technical measures to ensure IT security, including log management.
- German Commercial Code (HGB) and German Fiscal Code (AO): The HGB and the AO contain provisions on the retention of business records, including log data, for a certain period of time.
- Telecommunications Act (TKG): The TKG contains regulations on the security of telecommunications networks and services, including the collection and storage of log data.
Guidelines and standards: In addition to legal requirements, there are various guidelines and standards that relate to log management, such as ISO/IEC 27001 (information security management) and BSI-Grundschutz (IT security).
ProLog was developed specifically for critical infrastructures that demand the highest IT security standards. This means that CRITIS operators have a solution at hand that is tailored to their particularly high demands.
In addition, companies of any industry and size can use ProLog to meet all the requirements that an IT auditor places on log management. In this way, you master the technical and organizational requirements demanded by numerous laws and guidelines, such as:
- EU-DSGVO
- IT Security Act 2.0
- ISO 27001
- uvm.
To ensure the protection of personal data, ProLog works with the pseudonymization of data. Once an event is saved in ProLog's database, the personal reference is separated from it and stored elsewhere.
The personal reference of an event can be restored by depseudonymization, provided there is a valid reason for this under data protection law. ProLog handles such requests according to the n-eyes principle, where requests must receive approvals before depseudonymization can take place. Once the request has been approved, ProLog shows the requester the requested information. The personal reference for the event is temporarily restored according to the validity period of the request.
In addition, ProLog works with granular role concepts to avoid misuse in the system. This ensures that each user can only use the software for his specific activity.
With Log Management, all of your company's log data is collected in a central location, normalised and stored in a tamper-proof manner. Numerous regulatory requirements mandate the design and implementation of a log management solution. Learn more.
The Security Information and Event Management (SIEM) analyses and correlates this log data in real time. This allows complex events to be recognised in time, responsible persons to be informed by means of an alarm and countermeasures to be initiated.

Log data, also known as log files, log files or logs, are files in which computer processes log a wide variety of events. Logs are automatically generated by software, operating systems, network devices, and other IT components. They capture various types of information, such as user activity, login attempts, network connections, system events, error messages, security alerts, data accesses, and transactions.
Log Management enables the central collection, storage, monitoring and analysis of log data. This results in three important features that make Log Management important for your IT security:
- Detect threats early: By integrating log management solutions with SIEM systems, logs can be monitored in real time, analyzed, and matched against predefined rules or behavior patterns to identify potential threats.
- initiate countermeasures: In addition, vulnerabilities in IT systems can be identified and appropriate countermeasures can be taken.
- Forensic Analysis: Log management plays a critical role in forensic analysis of security incidents. By recording events in detail, logs enable the reconstruction of attacks, identification of entry points, and investigation of impact.
Every single company is exposed to the risks of a cybersecurity incident - regardless of the industry and the size of the company. That's why it basically makes sense for every company to ensure secure IT and implement a central log management system like ProLog.
However, "only" operators of critical infrastructures are currently legally obligated to do so.
According to Section 2(10) of the BSIG, this includes facilities, installations or parts thereof belonging to the following sectors:
- Energy
- Information technology and telecommunications
- Transportation and traffic
- Health
- Media and culture
- Water
- Nutrition
- Finance and insurance
- Municipal waste management
- State and administration
If your company does not fall under the BSI Criticality Ordinance, we still recommend that you set up your IT infrastructure securely and reliably. We will be happy to advise you on this.
In Germany, various legal requirements apply with regard to log management. These include, among others:
- General Data Protection Regulation (DSGVO): According to the DSGVO, personal data must be treated securely and confidentially. Log data that contains personal information is subject to the provisions of the DSGVO.
- Federal Data Protection Act (BDSG): The BDSG regulates the protection of personal data in Germany. It contains specific regulations on data security and the handling of log data.
- IT Security Act (IT-SiG): The IT-SiG obliges operators of critical infrastructures (KRITIS) to take appropriate organizational and technical measures to ensure IT security, including log management.
- German Commercial Code (HGB) and German Fiscal Code (AO): The HGB and the AO contain provisions on the retention of business records, including log data, for a certain period of time.
- Telecommunications Act (TKG): The TKG contains regulations on the security of telecommunications networks and services, including the collection and storage of log data.
Guidelines and standards: In addition to legal requirements, there are various guidelines and standards that relate to log management, such as ISO/IEC 27001 (information security management) and BSI-Grundschutz (IT security).
ProLog was developed specifically for critical infrastructures that demand the highest IT security standards. This means that CRITIS operators have a solution at hand that is tailored to their particularly high demands.
In addition, companies of any industry and size can use ProLog to meet all the requirements that an IT auditor places on log management. In this way, you master the technical and organizational requirements demanded by numerous laws and guidelines, such as:
- EU-DSGVO
- IT Security Act 2.0
- ISO 27001
- uvm.
To ensure the protection of personal data, ProLog works with the pseudonymization of data. Once an event is saved in ProLog's database, the personal reference is separated from it and stored elsewhere.
The personal reference of an event can be restored by depseudonymization, provided there is a valid reason for this under data protection law. ProLog handles such requests according to the n-eyes principle, where requests must receive approvals before depseudonymization can take place. Once the request has been approved, ProLog shows the requester the requested information. The personal reference for the event is temporarily restored according to the validity period of the request.
In addition, ProLog works with granular role concepts to avoid misuse in the system. This ensures that each user can only use the software for his specific activity.
